Ransomware has been the major cyber threat the last couple of years, and it still is! But a new trend I see is the rise of wiper malware, which basically tries to destroy your data, instead of encrypting it. This could be used as part of extortion, but we’ve all seen the recent news of how this kind of malware has been weaponized and turned into tools of warfare and conflict. If we fail to protect our data, keep up with good retention and backup hygiene, etc, then a wiper could inflict major damage on the organization.
I’m a big believer in demoing potential threats and vulnerabilities (I’ve learned the hard way that this is the single most effective way to get management to buy in on improving cyber security, next to experience a real breach of course). I recently blogged about a proof-of-concept tool I created called Invoke-DCM365DataExfiltration. It uses any poorly secured Azure AD app with file read permissions to exfiltrate large amounts of files from Microsoft Teams teams. I see this as a likely threat since so many tenants are missing proper app permission governance.
In this blog post I’m presenting a sister tool to Invoke-DCM365DataExfiltration called Invoke-DCM365DataWiper. The tool is part of my DCToolbox PowerShell module. The idea is to investigate if Microsoft 365 wipers is a real threat that we need to prepare for. Let’s have a look!
Invoke-DCM365DataWiper
This is a scary tool that tries to wipe all files from all teams in a Microsoft 365 tenant. It does this by leveraging any of the following Graph API application permissions (not delegated permissions) which are both commonly assigned to apps in an organization.
- Files.ReadWrite.All
- Sites.ReadWrite.All
I didn’t want to create a tool with too much power so it does not touch the recycle bin in SharePoint. You CAN restore files deleted by this tool, up to 93 days after the deletion. However, the Microsoft Graph API does not give us the possibility to restore files so it has to be done manually from the SharePoint GUI, or with the “legacy SharePoint API“. Note that the SharePoint API gives us the possibility to manage the recycle bin, and purge it, including the second stage recycle bin with no way of restoring the files! A more dangerous wiper than this can be created!
Example run:
Invoke-DCM365DataWiper -ClientID '' -ClientSecret '' -TenantName 'COMPANY.onmicrosoft.com' -WhatIf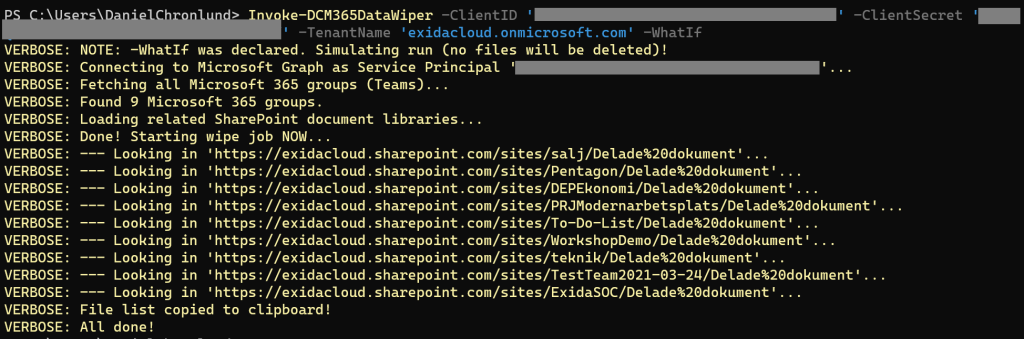
As you can see, the tool (simulating a run in this case) is going through all Microsoft Teams teams and their respective document libraries in the tenant. For each team, it deletes all found files, up to three folder levels down, and then exports a list of wiped files to the clipboard.
SharePoint Online Recycle Bin notes
Credits for this list goes to @gregoryzelfond
https://sharepointmaven.com/how-sharepoint-online-recycle-bin-works/
- Items in the Recycle bin are kept for 93 days (after the date they got deleted), then are permanently deleted and can no longer be restored
- The total threshold period of 93 days applies to both the “regular” Recycle bin and the Second-stage Recycle bin. So that means is that if the user decided to empty the Recycle Bin 5 days initially deleting items, they would be retained for 88 more days in the Second-stage recycle bin
- Each site has its own Recycle Bin. There is no catch-all Recycle bin
- Items located in the SharePoint Online Recycle Bin are not picked up by Search
Some screenshots of the manual restore process:



Are Microsoft 365 Wipers a Real Threat?
Since it is possible to delete files using an app registration, and purge the SharePoint recycle bin with the SharePoint API, I would say that this is a real threat. Threat actors are still learning to attack the cloud, and they’re getting better at it. I would not be surprised to see wiper malware targeting Microsoft 365 and teams in the near future.
So what can we do? Well, first of all I think it’s a good idea to setup retention policies in Microsoft 365. This makes sure data is retained for a certain amount of time, and it cannot be deleted by an app registration during that time. You can also use retention labels to classify specific SharePoint sites or individual files to retain them.
Backup solutions for Microsoft 365 exists and can protect some level of tenant content. Some years ago I wrote a blog post where I debated the need for such a solution. I would say that they provide protection, but it is not the first thing you should spend your cloud budget on. An E5 license with all its security and compliance features will provide you with important protection, not provided by a backup solution, in my opinion. It is not the same thing, but I rather manage a tenant with E5 than with a cloud backup solution attached. If you still have money left after the E5 investment, invest in a backup solution, but make sure it provides the same or better protection than Microsoft 365 itself, or it will become your weak spot. Think zero trust!
Conclusion
Wipers are on the rise, and the cloud will not likely be spared from this trend. Prepare by removing unnecessary API permissions from Azure AD apps, implement protection for Azure AD workload identities, make sure you set up proper retention, invest in your SIEM solution so that you can detect an attack in its early stage, and proactively hunt for threats in your tenant. Feel free to use this tool with the -WhatIf parameter and Files.Read.All permission (read-only) to evaluate and demonstrate the potential damage of a M365 wiper malware. Maybe it can lead to a bigger security budget 🙂
Please follow me here, on LinkedIn and on Twitter!