Introduction
Threat hunting is a great way to proactively look for suspicious behavior in your IT environment. Even though modern protection like EDR and ASR is important, it might not be enough against the advanced threats of today. You need to be more proactive! Hunting in Microsoft Sentinel makes it possible to bulk manage and bulk execute predefined KQL queries, designed for detecting anomalies and suspicious behaviors. Microsoft includes many hunting queries out-of-the-box, but the real strength is added when you create your own queries based on your specific needs.
As a security consultant, I’m monitoring many different unrelated Sentinel environments, and I needed a convenient way to store and manage my hunting queries centrally. I decided to create the DCSecurityOperations GitHub repo with Sentinel resources created from my own experiences and investigations. This makes it possible for other people to use it as well, if they find it useful. I will continuously add new and updates queries to this repo.
Please feel free to find inspiration for your own hunting queries, or simply deploy them as is.

Automatic Deployment
Prerequisites for automatic deployment:
- PowerShell 7.2 or later (winget install –id Microsoft.Powershell –source winget)
- git
- AZSentinel PowerShell module (Install-Module -Name AzSentinel -Scope CurrentUser -Force)
- powershell-yaml PowerShell module (Install-Module -Name powershell-yaml -Scope CurrentUser -Force)
Run the following in PowerShell to download and deploy (create and/or update) all Sentinel hunting queries in DCSecurityOperations:
# Clone the DCSecurityOperations GitHub repo.
git clone https://github.com/DanielChronlund/DCSecurityOperations
# Connect to Azure AD (requires at least the Sentinel Contributor role on the Sentinel resource group).
Connect-AzAccount
# Import/update all hunting queries from DCSecurityOperations.
Get-Item ".\DCSecurityOperations\Sentinel Hunting Queries\*.yaml" | Import-AzSentinelHuntingRule -WorkspaceName "NAME OF YOUR SENTINEL WORKSPACE"Note: Existing queries will be updated on import, as long as the name of the query is the same (something I’m trying to make sure).
You can also import individual hunting queries like this:
# Import/update a specific hunting query.
Import-AzSentinelHuntingRule -WorkspaceName "NAME OF YOUR SENTINEL WORKSPACE" -SettingsFile ".\DCSecurityOperations\Sentinel Hunting Queries\NAMEOFFILE.yaml"Manual Deployment
You can easily add a hunting query manually by copying the query from https://github.com/DanielChronlund/DCSecurityOperations/tree/main/Sentinel%20Hunting%20Queries to your Sentinel workspace.
Just copy the query:
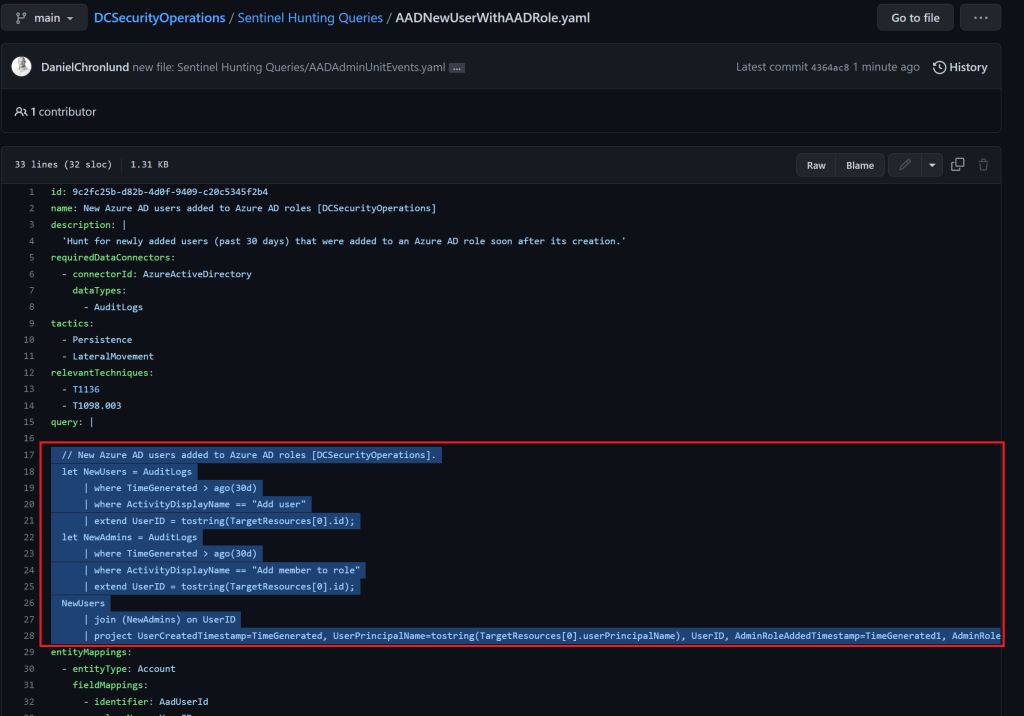
And paste it into a new hunting rule in Microsoft Sentinel:

Running the Hunting Queries
I’ve included a suffix on all hunting queries in DCSecurityOperations for easy filtering. Filter on DCSecurityOperations, mark all search results, and click Run selected queries. That’s it, check the results of each query where the Results column is greater than 0.
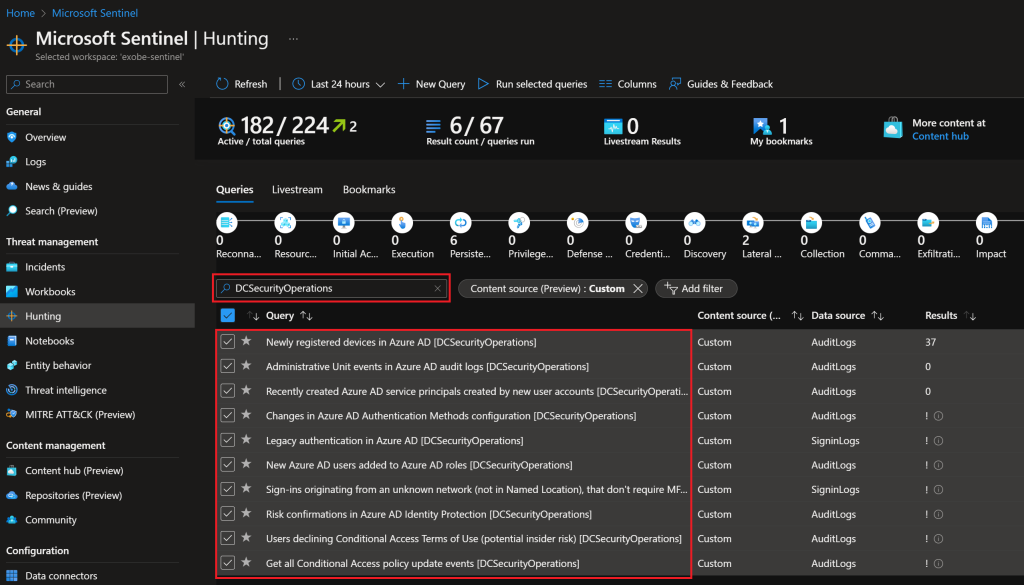
Make sure you check back from time to time as this collection of hunting rules will grove over time. Happy hunting!
Please follow me here, on LinkedIn and on Twitter!
2 thoughts on “Sentinel Hunting Query Pack – DCSecurityOperations”