Managing Conditional Access polices in Entra ID at scale can be a real hassle. The GUI-based management tools were not designed to perform any kind of configuration in bulk. I decided to automate some of the most common bulk management tasks in Conditional Access management and put them into DCToolbox. These tools will sure save a lot of time for anyone deploying and managing Conditional Access at scale.
In this blog post I will demonstrate these tools with examples. Before you try this at home, please install/update DCToolbox to the latest version:
# Install / update DCToolbox:
Install-Module -Name DCToolbox -ForceGreat! And all of the examples in this blog post can also be accessed with:
Copy-DCExampleNote that I’m a fan of using different kinds of name prefixes to treat multiple Conditional Access policies as a group. This makes it easy to target bulk actions to many policies at ones. Now, let’s get started.
Task 1: Bulk toggle between ‘Report-only’ and ‘Enabled’
Before you deploy your Conditional Access policies you often run them in report-only mode. When it is time to enable them you usually must edit each policy on by one. Not anymore!
# Toggle specified Conditional Access policies between 'Enabled' and 'Report-only'.
Set-DCConditionalAccessPoliciesReportOnlyMode -PrefixFilter 'GLOBAL - ' -SetToReportOnly
# Toggle specified Conditional Access policies between 'Report-only' and 'Enabled'.
Set-DCConditionalAccessPoliciesReportOnlyMode -PrefixFilter 'GLOBAL - ' -SetToEnabled
Task 2: Bulk toggle between a pilot group and ‘All users’
When you deploy Conditional Access policies for the first time, or in parallell with an existing policy design, you commonly use security groups to include and exclude users during the pilot phase. This is a flexible approach since you can target individual pilot users.
However, when you move between pilot and production phase, it can be daunting to change all Conditional Access policies manually. This will help you with this specific step:
# Toggle Conditional Access policies between 'All users' and specified pilot group.
Set-DCConditionalAccessPoliciesPilotMode -PrefixFilter 'GLOBAL - ' -PilotGroupName 'Conditional Access Pilot' -EnablePilot
# Toggle Conditional Access policies between specified pilot group and 'All users'.
Set-DCConditionalAccessPoliciesPilotMode -PrefixFilter 'GLOBAL - ' -PilotGroupName 'Conditional Access Pilot' -EnableProduction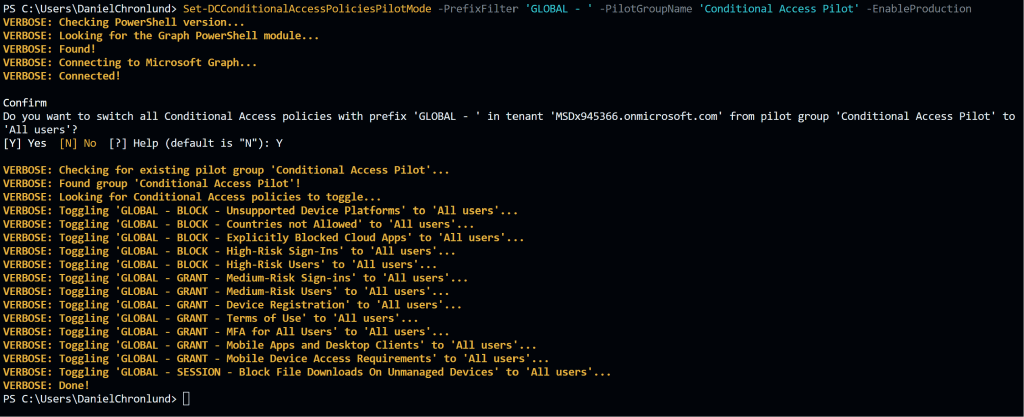
Task 3: Bulk add a break glass security group to ALL existing Conditional Access policies
The first thing you should do before modifying any Conditional Access implementation is to make sure you have emergency access in case something goes wrong. Always include a role assignable security group containing your break glass accounts. It should be role assignable (without any roles assigned) so that only Global Admins can manage its members.
To make it easy and fast to add your break glass group to all existing Conditional Access policies, I created this tool. Make it a habit to run it before performing any other work with Conditional Access:
# Exclude a specified break glass group from all Conditional Access policies.
Add-DCConditionalAccessPoliciesBreakGlassGroup -PrefixFilter 'GLOBAL - ' -ExcludeGroupName 'Excluded from Conditional Access'
Task 4: Bulk remove ALL Conditional Access polices from tenant (be careful!)
When you manage Conditional Access policies at scale, you often find yourself in a situation where you want to delete all or a set of Conditional Access policies in a tenant. Examples of such situations are:
- Cleaning up your test tenant.
- Removing all pilot/test polices after broad deployment.
- Red Team: Disarming an Entra ID tenant during an attack.
This tool can help you automate large scale policy removal, which is a common part of the test/pilot phase:
# Delete ALL Conditional Access policies.
Remove-DCAllConditionalAccessPolicies
# Delete all Conditional Access policies with a specific prefix.
Remove-DCAllConditionalAccessPolicies -PrefixFilter 'OLD - '
# Delete all Conditional Access policies WITHOUT a specific prefix (like -PrefixFilter but reversed).
Remove-DCAllConditionalAccessPolicies -ReversedPrefixFilter 'GLOBAL - '
Task 5: Bulk rename Conditional Access policies
Finally, renaming Conditional Access policies is quite common if you manage them in bulk, specifically adding and removing prefixes.
# Rename Conditional Access policies.
Rename-DCConditionalAccessPolicies -PrefixFilter 'PILOT - ' -AddCustomPrefix 'PROD - '
# Add a prefix to specific Conditional Access policies.
Rename-DCConditionalAccessPolicies -PrefixFilter 'GLOBAL - ' -AddCustomPrefix 'OLD - GLOBAL - '
# Add a prefix to ALL existing Conditional Access policies.
Rename-DCConditionalAccessPolicies -AddCustomPrefix 'OLD - '
I hope this will help you to manage Conditional Access policies at scale.
Please follow me here, on LinkedIn, and on X!